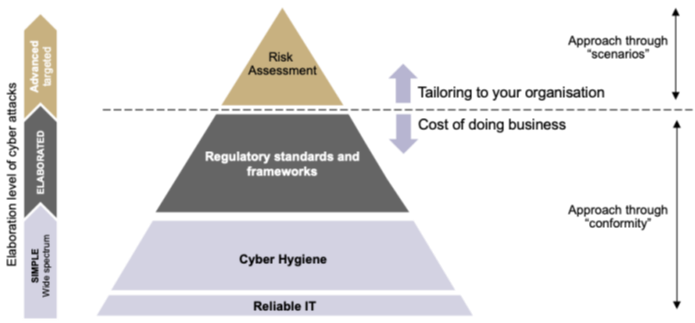
Do organisations apply ROSI in practice?
As part of the AMS research tracks on Cybereconomics, we conducted surveys and interviews with practitioners to assess whether they use economic modelling to justify cybersecurity investment decisions and communicate these decisions to boards. Surprisingly, the majority reported that they do not apply ROSI in practice. ROSI, or Return on Security Investment, is a financial metric that evaluates the monetary benefit of security measures. It measures the value by comparing the cost of
implementing security solutions to the potential losses prevented, considering both tangible and intangible avoided costs. Essentially, it calculates the economic gain from a security investment by assessing risk reduction and cost savings against total security expenses. When asked why they don’t utilize ROSI, respondents typically cite four main challenges:
• Quantifying risks and risk reduction is difficult due to complexity and a lack of actuarial data.
• Limited analytical capabilities are often linked with the perception that complex mathematical calculations are necessary.
• Lack of time and resources to perform quantitative analyses.
• Organisational culture and preferences. Case organisations report that decision-making in IT and/or cybersecurity, based on quantification, is not part of the organisation's culture.
Leaving cultural aspects aside, the first three obstacles stem largely from perceptions of complexity associated with quantitative methods, such as ROSI. This finding prompts a closer examination of Cyber Risk Quantification (CRQ) adoption.
The problem: the perceived complexity of cyber risk quantification This perceived complexity, rather than actual mathematical difficulty, hinders the adoption of risk quantification. In many cases, organisations describe their cyber investment decision-making as based on a combination of industry benchmarks and “gut feeling”. Complementary research conducted by AMS students confirms that most organisations rely on qualitative or mixed methods, despite ~75% of respondents considering CRQ feasible, and all agreeing that quantification would enhance decision-making. A practical starting point is to replace qualitative labels with quantitative proxies and to express uncertainty as ranges rather than fixed numbers.